
This week I install pfBlocker-NG on a pfSense firewall. I did not activate every feed in the IP (black list) category. Only a few like the CINS Army, Abuse SSL Blacklist and Spamhaus.
The IP’s protected by this firewall is from a commercial service (Fixed IP) but there is very little (almost none) traffic to the web site and email at this address.
Anyway, as they say an image worth a thousand words so this is the number of packets that has been blocked in 48 hours.
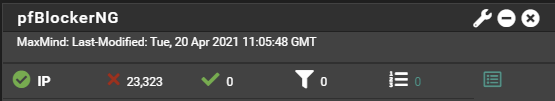
I remember well that in the beginning of the years 2000 I was managing a firewall to protect a customer who was a major in his business field. At that time the firewall was blocking more than 2000 attacks a day all coming from IP in China. It was, in my point of view, clearly attempt to steal industrial secrets.
But this day’s any kids on the block can use Ubuntu to create bot and the most advanced hackers will use Kali Linux to do unwanted large scale penetration test. Those packets (in the image above) have been blocked out of an IP that ends at a very low bandwidth commercial internet connection. The services provided are not hosted in a data center and/or with connection direct on the backbone.
This led me to think, this is what we are seeing at a relatively easy place to logs and tracks IP connections. But what if we were to do the same on our cellular phone connection? Your are welcome to post the (anonymized) packets block logs coming from a regular cellular phone like all of us are now using.
Since a little while, I do now close the internet connection on my cellular when not needed, but let’s admit it, I didn’t not so long ago and most of the people without knowledge in IT and security keep it open 24/7 even while they are sleeping.
Did I say while they are sleeping?
Like Led Zeppelin say in Stairway to Heaven, « ‘Cause you know sometimes words have two meanings”. And I do think that this is not buying a Stairway to Heaven in any way. Not to the advantage of the cellular owner at least… This make me wonder what will it be once every new company on the blocs integrate a cheap and weak IP stack to their stuff to surf and market new ‘’hot trend’’ out of things to turns it in IoT?

1 Trackback / Pingback