
EDGE transport server installation by default comes with a self-signed certificate.
This article public SSL (TLS) certificate for your EDGE transport server.
Run this cmdlet to get details on the certificate currently installed on the EDGE server:
Get-ExchangeCertificate |flYou may see:
IsSelfSigned : True
Issuer : CN=ServerName
Create a new CSR (Certificate Signing Request) from Exchange Management Shell
Use the following cmdlet:
New-ExchangeCertificate -GenerateRequest -Domainname mydomain_dot_com -PrivateKeyExportable $True >>c:\CSRreq.txtUse CSR to request a public SSL certificate from your favorite SSL broker.
Import the cert to EDGE server
Now let’s navigate back to the EDGE server and import this new cert from C:\mydomain_dot_com.cer
Use the cmdlet:
Import-ExchangeCertificate -FileData ([Byte[]]$(Get-Content -Path C:\mydomain_dot_com.cer -Encoding byte -ReadCount 0))If it succeed, let’s proceed to the next step:
Enable-ExchangeCertificate -Thumbprint A43542033E3F6603CFBEFF51C6EEF12487101606 -Services SMTPNow, the edge subscription has to be renew because the certificate has been changed on the mailbox or DAG server.
First let’s remove the current edge subscription from the internal Mailbox Servers. Execute the following command by using the Exchange Management Shell on one of the Mailbox Servers. This will remove the Subscription for the whole Active Directory Site they assigned to.
Remove-EdgeSubscription | Get-EdgeSubscriptionNow that the Edge Subscription is removed, we need to create a new Edge Subscription on the Edge Server and afterwards import that on one of the internal Mailbox Servers.
Execute the following command to create the new Edge Subscription in the Exchange Management Shell on the Edge Server.
New-EdgeSubscription -FileName “c:\EdgeServerSubscription.xml”Next copy the created Edge Subscription file (EdgeServerSubscription.xml) to one of the internal Mailbox Servers in order to import that subscription.
Now we have to run the following command on that internal Mailbox Server and its Exchange Management Shell.
New-EdgeSubscription -FileData ([byte[]]$(Get-Content -Path "C:\EdgeServerSubscription.xml" -Encoding Byte -ReadCount 0)) -Site "Default-First-Site-Name"If different from default settings, replace Default-First-Site-Name with your AD Site by the main site you want to renew the subscription.
You can determine the names of your AD Sites by using the Get-ADSite command as follows.
Get-ADSiteAs shown in the warning, the internal Mailbox Servers needs to be able to resolve the FQDN of the Edge Server into its correct IP and also need to be able to connect to it through TCP Port 50636.
As I will only update the subscription these requirements of course still in place.
To check them anyway, I prefer the old school style by using telnet which will perform by default a TCP three–way–handshake to the destination FQDN or IP and port number.
telnet edge.mydomain.dot.com 50636Now we can start the synchronization with the Edge Server on one of the internal Mailbox Server as follows to check if it works.
Start-EdgeSynchronization
To verify if the new edge registration succeed use this command:
Test-EdgeSynchronization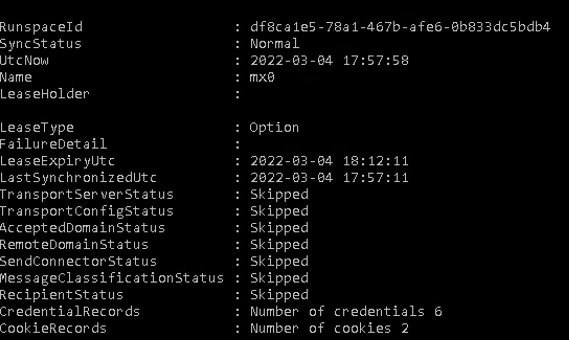
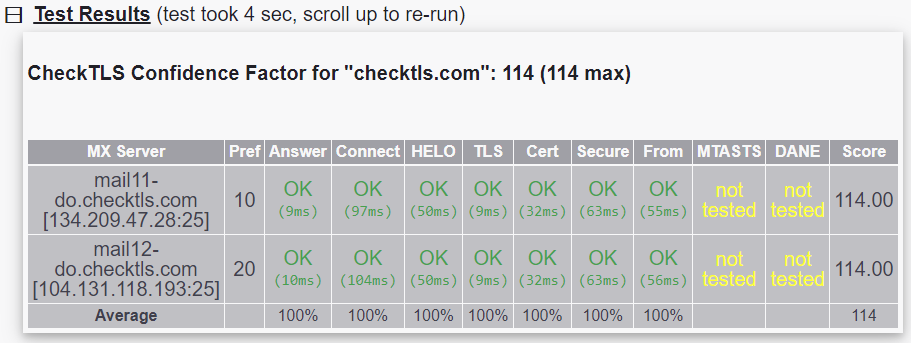
Finally, you can verify how you get your encrypted email using Check TLS.
Here is a copy of the result with the Check TLS email servers


Be the first to comment