
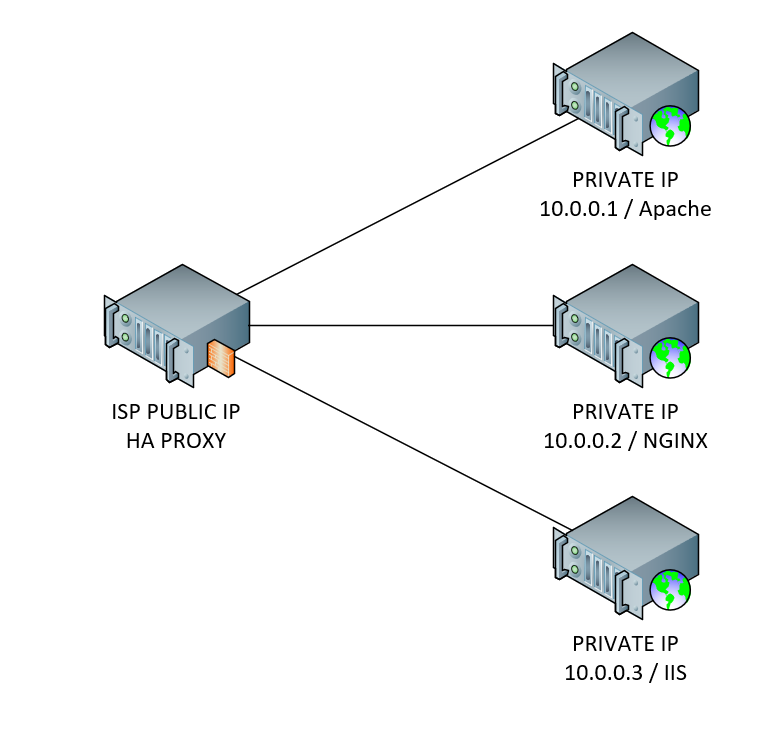
What is a reverse proxy?
A reverse proxy is a server that sits in front of web servers and forwards client (e.g. web browser) requests to those web servers. Reverse proxies are typically implemented to help increase security, performance, and reliability.
HA PROXY
HAProxy is a free, very fast and reliable reverse-proxy offering high availability, load balancing, and proxying for TCP and HTTP-based applications. It is particularly suited for very high traffic web sites and powers a significant portion of the world’s most visited ones. Over the years it has become the de-facto standard opensource load balancer, is now shipped with most mainstream Linux distributions, and is often deployed by default in cloud platforms.
CONFIG FILE EXAMPLE
The file name is haproxy.cfg in /etc/haproxy/
#---------------------------------------------------------------------
# Example configuration for a possible web application. See the
# full configuration options online.
#
# https://www.haproxy.org/download/1.8/doc/configuration.txt
#
#---------------------------------------------------------------------
#---------------------------------------------------------------------
# Global settings
#---------------------------------------------------------------------
global
user haproxy
group haproxy
daemon
chroot /var/lib/haproxy
pidfile /var/run/haproxy.pid
# Use to limit to many request send to a backend server
maxconn 50000
# utilize system-wide crypto-policies
ssl-default-bind-ciphers PROFILE=SYSTEM
ssl-default-server-ciphers PROFILE=SYSTEM
ssl-default-bind-ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-P$
ssl-default-bind-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
ssl-default-bind-options no-sslv3 no-tlsv10 # no-tlsv11 no-tls-ticketsssl-default-server-ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20$
ssl-default-server-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
ssl-default-server-options no-sslv3 no-tlsv10 no-tlsv11 no-tls-tickets
#---------------------------------------------------------------------
# common defaults that all the 'listen' and 'backend' sections will
# use if not designated in their block
#---------------------------------------------------------------------
defaults
mode http
log global
option httplog
option dontlognull
option http-server-close
option forwardfor except 127.0.0.0/8
option redispatch
retries 3
timeout http-request 10s
timeout queue 1m
timeout connect 10s
timeout client 1m
timeout server 1m
timeout http-keep-alive 10s
timeout check 10s
maxconn 100000
#---------------------------------------------------------------------
# main frontend statistique URL
#---------------------------------------------------------------------
listen STATISTICS
bind *:8086
mode http
stats enable
stats uri / #stats
stats refresh 5s
stats hide-version # Hide HAProxy version
stats realm Haproxy\ Statistics # Title text for popup window
stats auth Admin:Netstat # Authentication credentials
default_backend be_APACHE
#---------------------------------------------------------------------
# main frontend which proxys to the backends
#---------------------------------------------------------------------
frontend fe_HTTP
mode http
option forwardfor
# TDL ACL
acl apachehosteddomain.com hdr(host) -m dom apachehosteddomain.com
acl nginxhosteddomain.com hdr(host) -m dom nginxhosteddomain.com
acl iishosteddomain.com hdr(host) -m dom iishosteddomain.com
# Sub Level Servers ACL
acl subdomain.apachehosteddomain.com hdr(host) -m dom subdomain.apachehosteddomain.com
acl subdomain.nginxhosteddomain.com hdr(host) -m dom subdomain.nginxhosteddomain.com
acl subdomain.iishosteddomain.com hdr(host) -m dom subdomain.iishosteddomain.com
## HTTP
# listen for HTTP traffic
bind *:80
# Redirect to WWW
redirect prefix http://subdomain.apachehosteddomain.com code 301 if { hdr(host) -i subdomain.apachehosteddomain.com }
redirect prefix http://subdomain.nginxhosteddomain.com code 301 if { hdr(host) -i subdomain.nginxhosteddomain.com }
redirect prefix http://subdomain.iishosteddomain.com code 301 if { hdr(host) -i subdomain.iishosteddomain.com }
# HTTP to SSL Redirect
redirect scheme https code 301 if !{ ssl_fc } subdomain.apachehosteddomain.com
redirect scheme https code 301 if !{ ssl_fc } subdomain.nginxhosteddomain.com
redirect scheme https code 301 if !{ ssl_fc } subdomain.iishosteddomain.com
# SSL Offloading
# listen for HTTPS traffic, load certificates from a directory,
bind *:443 ssl crt-list /etc/haproxy/certs/crt-list.txt alpn h2,http/1.1
http-response set-header Strict-Transport-Security max-age=16000000;\ includeSubDomains;\ preload;
# Set Client IP for backend server
option forwardfor header X-Real-IP
http-request set-header X-Real-IP %[src]
option forwardfor header X-Client-IP
http-request set-header X-Client-IP %[src]
# subdomain.apachehosteddomain.com SSL
# Inform backend the client connect via HTTPS - Full HTTPS Client - Proxy - Server
http-request set-header X-Forwarded-Proto https if subdomain.apachehosteddomain.com
# subdomain.nginxhosteddomain.com SSL
# Inform backend the client connect via HTTPS - Full HTTPS Client - Proxy - Server
http-request set-header X-Forwarded-Proto https if subdomain.nginxhosteddomain.com
# subdomain.iishosteddomain.com SSL
# Inform backend the client connect via HTTPS - Full HTTPS Client - Proxy - Server
http-request set-header X-Forwarded-Proto https if subdomain.iishosteddomain.com
# APACHE backend
use_backend be_APACHE if apachehosteddomain.com
use_backend be_APACHE if subdomain.apachehosteddomain.com
# NGINX backend
use_backend be_NGINX if nginxhosteddomain.com
use_backend be_NGINX if subdomain.nginxhosteddomain.com
# IIS backend
use_backend be_IIS if iishosteddomain.com
use_backend be_IIS if subdomain.iishosteddomain.com
#---------------------------------------------------------------------
# Backend server for APACHE HTTP/HTTPS services
#---------------------------------------------------------------------
backend be_APACHE
mode http
compression algo gzip
http-response set-header Content-Security-Policy upgrade-insecure-requests
server APACHE 10.0.0.1:80 check maxconn 5000
#---------------------------------------------------------------------
# Backend server for NGINX HTTP/HTTPS services
#---------------------------------------------------------------------
backend be_NGINX
mode http
compression algo gzip
http-response set-header Content-Security-Policy upgrade-insecure-requests
server NGINX 10.0.0.2:80 check maxconn 5000
#---------------------------------------------------------------------
# Backend server for IIS HTTP/HTTPS services
#---------------------------------------------------------------------
backend be_IIS
mode http
compression algo gzip
http-response set-header Content-Security-Policy upgrade-insecure-requests
server IIS 10.0.0.3:80 check maxconn 5000

Be the first to comment